Table of Contents

When your organization retires IT hardware, proper data destruction isn’t optional – it’s essential. A single data breach can cost companies millions in fines, legal fees, and reputational damage. Certified data destruction provides the security and compliance documentation your business needs to protect sensitive information and meet regulatory requirements.
This comprehensive guide walks you through everything you need to know about certified data destruction, from understanding key standards to selecting the right service provider for your organization.
Understanding Data Destruction Certification
Certificates of Destruction are documents that formally verify that sensitive information stored on electronic devices has been completely and irreversibly destroyed according to established security standards. This process involves more than simply deleting files or formatting drives- it requires specialized techniques and documentation to ensure data cannot be recovered.

The Importance of Certified Data Destruction
Organizations handle vast amounts of sensitive data daily, from customer information to proprietary business secrets. When IT equipment reaches end-of-life, this data remains accessible unless properly destroyed. Standard deletion methods don’t actually remove data from storage devices; they simply mark space as available for overwriting.
Professional data destruction services use specialized methods to ensure complete data elimination. These services provide certificates of destruction that serve as legal proof of compliance with data protection regulations.
Learn more about our Data Destruction services to ensure your data storage devices are thoroughly destroyed.
Risks of Improper Data Disposal
Inadequate data handling exposes organizations to serious risks:
Financial Penalties: Regulatory violations can result in substantial fines. GDPR violations alone can cost up to 4% of annual global revenue or $23 million, whichever is higher.
Legal Liability: Businesses may face lawsuits from affected customers or partners if sensitive data is compromised due to improper disposal.
Reputational Damage: Data breaches erode customer trust and can impact business relationships for years.
Competitive Disadvantage: Proprietary information in the wrong hands can harm your competitive position.
Understanding Data Destruction Standards & Regulations
Multiple regulatory frameworks govern data destruction requirements across different industries and regions. Understanding these standards is crucial for maintaining compliance.

Key Data Protection Standards
NIST (National Institute of Standards and Technology): NIST SP 800-88 provides guidelines for media sanitization, outlining specific methods for different storage technologies. This standard is widely adopted across federal agencies and private organizations.
These standards include:
- Clear: Overwrite Data
- Purge: Cryptographic Erasure
- Destroy: Physically Destroy
- Validate: Full Documentation
Read our full NIST 800-88 guide here.
IEEE (Institute of Electrical and Electronics Engineers): IEEE 2883-2022 provides comprehensive guidelines for securely sanitizing physical and digital storage devices through methods like overwriting, degaussing, and physical destruction, ensuring data is irretrievable and compliance is maintained.
The Institute of Electrical and Electronics Engineers standards include:
- Clear: Overwrite Data
- Purge: Cryptographic erasure while preserving the storage device in a reusable state.
- Destroy: Physically Destroy
GDPR (General Data Protection Regulation): European regulations require organizations to implement appropriate technical measures to ensure data security, including secure deletion when data is no longer needed.
The General Data Protection Regulations applies to data of those in the EU and includes:
- Data Protection Rights: Safeguards personal data
- Consent & Transparency: Requires clear user consent
- Accountability & Compliance: Enforces strict regulations
SOX (Sarbanes-Oxley Act): Financial organizations must maintain strict controls over financial data, including secure destruction of records containing sensitive financial information.
The Sarbanes-Oxley Act, a US law, includes the following standards:
- Financial Reporting Accuracy: Ensures truthful disclosures
- Internal Controls: Mandates robust systems
- Accountability & Audits: Enforces compliance checks
PCI DSS (Payment Card Industry Data Security Standard): Companies handling credit card data must follow specific requirements for secure data disposal to maintain PCI compliance.
The Payment Card Industry Data Security Standards include:
- Cardholder Data Protection: Secures payment info
- Access Control: Limits data access
- Regular Monitoring: Ensures ongoing compliance
HIPAA (Health Insurance Portability and Accountability Act): Healthcare organizations must follow HIPAA requirements for protecting patient information throughout its lifecycle, including secure disposal of electronic media containing protected health information.
The Health Insurance Portability and Accountability Act standards include:
- Patient Data Privacy: Protects health information
- Security Safeguards: Ensures data protection
- Compliance Enforcement: Mandates strict adherence
Read more about these data destructions standards here.
Why Compliance is Crucial for Businesses
Regulatory compliance isn’t just about avoiding penalties – it’s about maintaining operational integrity and customer trust. Compliance requirements vary by industry, but all organizations benefit from following established data destruction standards.
Proper certification demonstrates due diligence in protecting sensitive information. This documentation proves your organization took appropriate steps to prevent data breaches, which can be crucial in legal proceedings or regulatory audits.
Methods of Certified Data Destruction
Different data destruction methods are appropriate for various storage technologies and security requirements. Understanding these options helps you choose the most suitable approach for your organization.
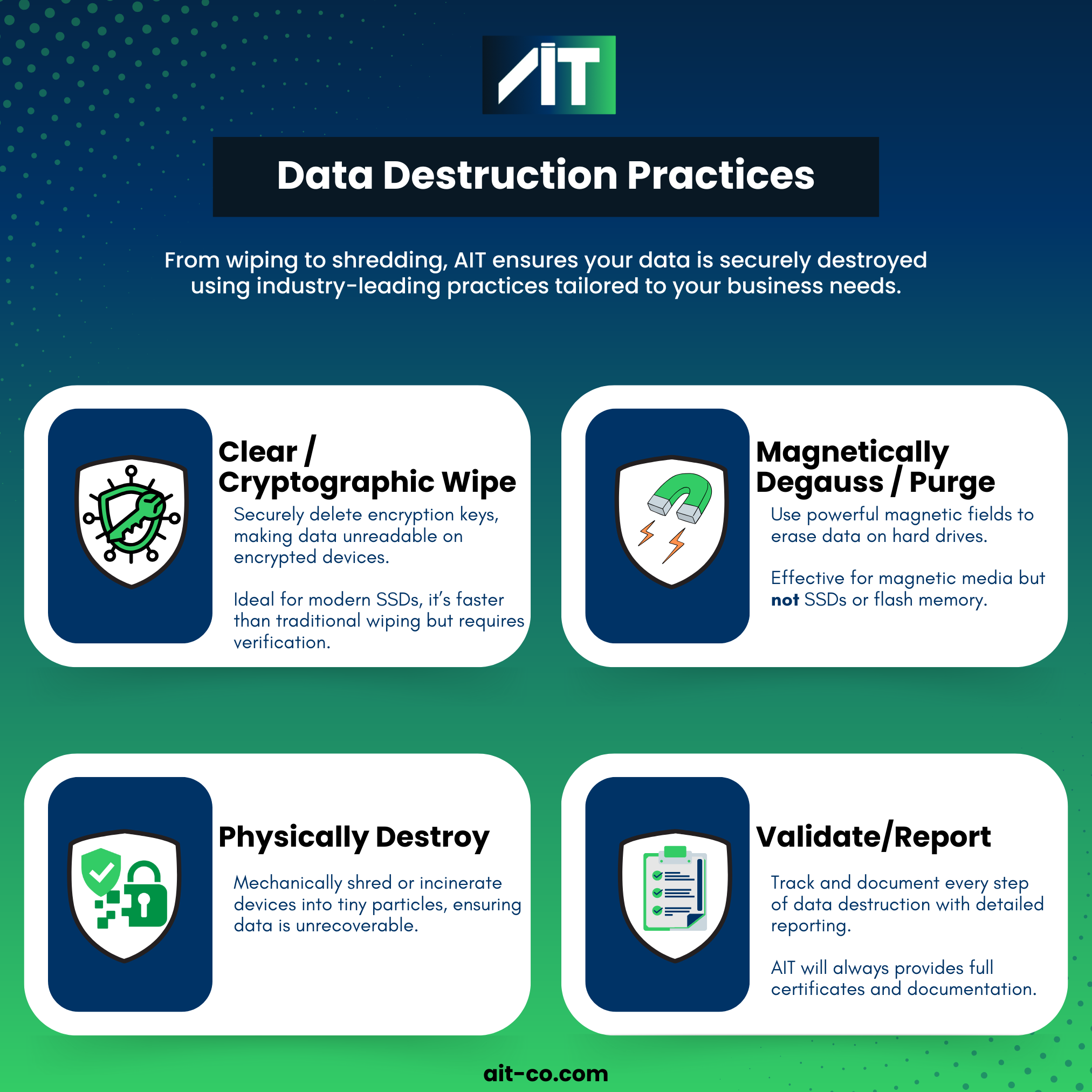
Clear/Cryptographic Wipe
For encrypted storage devices, cryptographic wiping involves securely deleting encryption keys, making data unreadable even if the underlying information remains on the device. This method is particularly effective for modern SSDs with hardware encryption.
The process is faster than traditional data wiping but requires verification that encryption was properly implemented and keys are irretrievably destroyed.
Magnetically Degauss/Purge
Degaussing uses powerful magnetic fields to disrupt the magnetic domains on traditional hard drives, rendering data unrecoverable. This method is effective for magnetic storage media but doesn’t work on solid-state drives (SSDs) or flash memory.
The process involves exposing storage devices to magnetic fields thousands of times stronger than typical household magnets. Certified degaussing equipment meets specific standards for magnetic field strength and uniformity.
Physical Shred
Physical shredding or incinerating destroys storage devices into small particles, making data recovery impossible. Industrial shredders reduce hard drives, SSDs, and other media to particles smaller than 2mm.
This method is effective for all storage technologies and provides visual confirmation of destruction. The resulting particles are typically recycled as raw materials, supporting environmental sustainability goals.
Validate
Validation ensures every step of the data destruction process is documented and tracked. Devices are scanned for detailed reporting, creating a comprehensive paper trail of services performed. This not only supports regulatory compliance but also provides peace of mind with verifiable proof of secure data destruction.
AIT recommends using a combination of asset scanning, clearing, degaussing,and then destroying hard drives for maximum security. AIT will always provide Certificates of Destruction and a full recycling report for full transparency throughout the recycling process.
Read more about AIT’s Reporting & Certificates here.
Onsite vs. Offsite Destruction
Onsite Destruction: Mobile destruction services bring equipment directly to your facility, allowing you to witness the destruction process. This method provides maximum security and peace of mind, particularly for highly sensitive data.
Advantages include:
- Complete control over the destruction process
- Immediate certificate of destruction
- Ability to witness destruction firsthand
Offsite Destruction: Equipment is transported to a secure facility for destruction. This method may be more cost-effective for large volumes but requires careful chain-of-custody procedures.
Benefits include:
- Lower costs for high-volume destruction
- Access to specialized equipment
- Environmentally controlled facilities
- Comprehensive recycling services
Choosing a Certified Data Destruction Provider
Selecting the right data destruction provider is crucial for ensuring security and compliance. Several factors should guide your decision.
Essential Provider Qualifications
Industry Certifications: Look for providers who meet the following compliance standards:
- NAID (National Association for Information Destruction) compliant
- R2 (Responsible Recycling) compliant
- ISO 27001 information security management compliant
AIT is compliant with all of the above and more. Ensure your data is securely destroyed with AIT’s Certified Data Destruction Services or contact us now to get started today.
Ensuring Secure Chain of Custody
A secure chain of custody tracks IT assets from pickup through final destruction. This documentation is essential for compliance and audit purposes.
Key elements include:
- Detailed asset inventories
- Tamper-evident transportation and containers
- Continuous scanning and monitoring of assets
- Comprehensive documentation at each step
Your provider should maintain detailed records of who handled assets, when transfers occurred, and what security measures were in place throughout the process. AIT will always provide you with a full e-waste recycling report with full details of the materials you have recycled and how much.
Reporting and Documentation
Comprehensive documentation is essential for proving compliance and maintaining audit trails. Your provider should deliver:
Certificate of Destruction: Legal document confirming complete data destruction, including details about methods used and dates of destruction.
Detailed Asset Reports: Comprehensive listings of all destroyed devices with serial numbers and destruction methods.
Full E-waste Report: Complete tracking documentation from pickup through final disposal.
Discover our Reporting & Documentation services for comprehensive compliance records that support your audit and regulatory requirements.
Securing Your Data’s Final Chapter
Certified data destruction is a critical component of comprehensive data security strategy. By understanding regulatory requirements, choosing appropriate destruction methods, and selecting a , organizations can protect sensitive information while maintaining compliance with applicable standards.
The investment in certified data destruction services pays dividends through reduced legal risks, enhanced security, and improved environmental responsibility. As data protection regulations continue to evolve, working with experienced providers ensures your organization stays ahead of compliance requirements.
Ready to secure your retired IT assets with certified data destruction? Contact AIT today to discuss customized solutions tailored to your organization’s specific needs and regulatory requirements.